
The Road to Cybersecurity Maturity
IT STARTS HERE
The road to cybersecurity maturity can be daunting.
You don't have to walk it alone.We have helped many organizations define their roadmap to cybersecurity maturity; empowering boardrooms to make strategic decisions around security while preserving organizational performance.
Select a location from the list on the right, and let's chat to see if we're a good fit to support you along your journey.
Pick your city, pick your time, and let's talk. No charge for the chat.
Schedule a Virtual Chat with Us

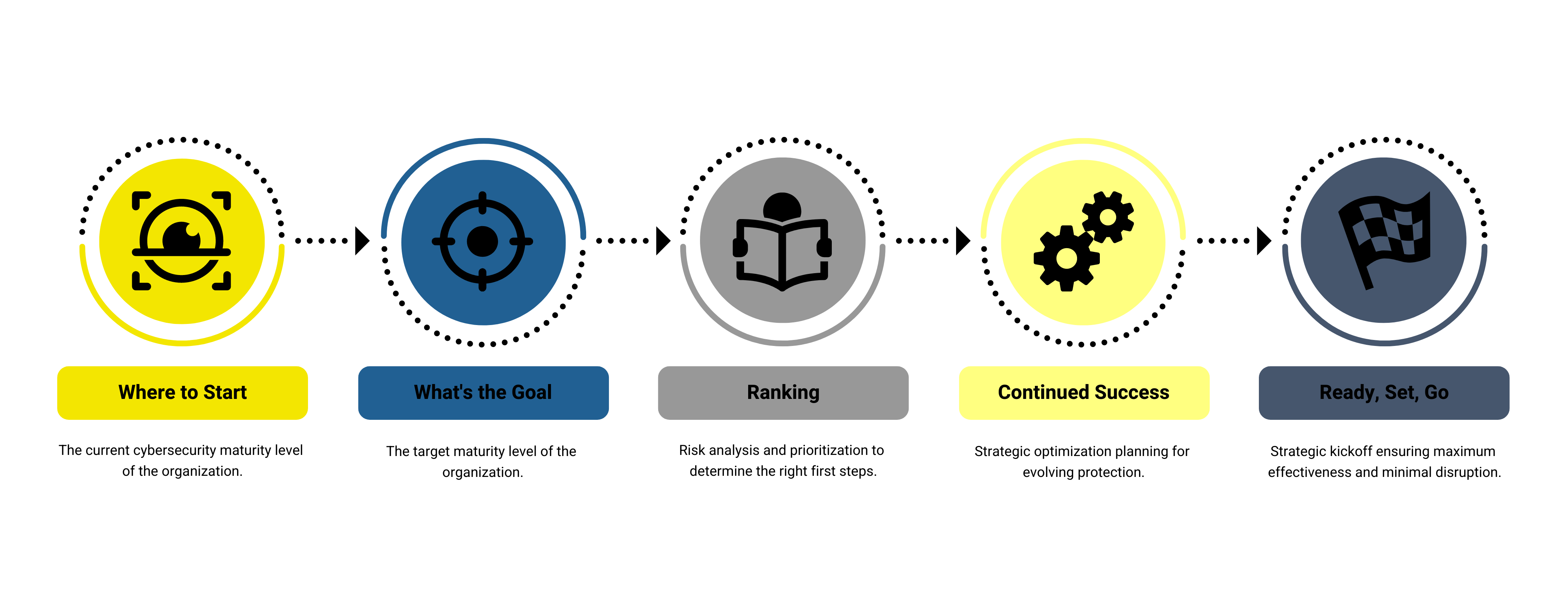
Maturity Assessment Deliverables
Components of a Mature Security Culture
Security-First Leadership
Leading with a security-first mindset means that security is at the forefront of every strategic decision of the business. Smart businesses consult with their security teams before a solution is deployed. Security-First organizations consider security in every step of their executive decision making process. Elevating security from a check-step to a component of strategic thinking is a clear sign of a mature security culture.
Innovation and Transparency
Visible and effective security technology deployments reinforce the standards of behaviour. Taking it one step further, and sharing the "why" of the deployment with all members of the organization will create a shared value of the importance of upholding the integrity of security deployments.
Shift from the Blame Game
You will get breached. A Cyber Mature organization is one that promotes an employee alert system, and rewards those who report issues. When a potential breach occurs, it can be dealt with swiftly and immediately, as opposed to a lengthy investigation looking for an incident whereby an employee was too afraid to report an incident.
Education, Communication, and Testing
Vigilance and repetition are the catch words of success. A great way to ensure both is by creating a sound User Awareness Program. This program should include high quality education content, an active testing component, progress reporting, and industry benchmarking.
Hope for the Best, Prepare for the Worst
A mature cybersecurity culture invests time, energy, and resources into Response and Recovery planning. Prevention solutions are important to mitigate risks and damage, but, as stated earlier, you WILL get breached. How will you respond?
